Dec 4, 2024
Your Diligence Deserves Better – Predatory Journals Explained
Research

The sources you choose for your diligence impact the outcome of your diligence project. Relying on questionable sources can lead to flawed outcomes. A type of source to avoid is predatory journals. Learn how to spot them and why you should avoid them.
Why it Matters ?
Sources matter. Your diligence conclusions are reliant on the quality of your original sources. So you want to start your project with quality sources and you also don’t want to waste time trying to decide if a source is worth your time. One way to speed up your source evaluation is to learn to recognize categories of sources to avoid.
First, it is important to understand why you are in the position of having to do this? The answer is that for much of the recent past we have been able to rely on gatekeepers to vet sources and content. This is especially true in the areas of professional or specialized fields such as science, law, engineering, medicine and academics. Those areas had established frameworks that resulted in curated bodies of work. If you were conducting research your job was to look at the curated body of work and choose the most appropriate sources for your own project.
This is no longer the case, the gatekeepers no longer control the environment in which this type of content is produced, now we have to have the skills and instincts needed to separate what is real and useful from what is fake or junk.
The Role and Value of Gatekeepers
Traditionally, for content to be released for public consumption it had to pass through gatekeepers. Gatekeepers were instrumental in establishing and maintaining quality. These gatekeepers could be:
- an industry for example, publishing, mainstream broadcasting
- publishers
- editors
- experts
- peers
- aggregators of content such as source databases and news aggregators
- individuals such as librarians charged with making informed source choices for their collections
They provided a series of “gatekeeping functions” by establishing and enforcing standards and procedures for the creation, submission, editing, publication and even correction and retraction of content. This resulted in a framework that was knowable to an end user and that the end user relied upon as an acknowledgement of quality.
In fact, this framework was developed to not only to decide what was published but also to insure that creators understood what type of content would be accepted into the system.
The net effect of this system was that an end users source and therefore content choices were limited but it was reasonable to expect that the sources and content were reputable and met certain standards.
Without Gatekeepers Predators Move In
The source and content world is now very different, the invention and growth of the internet, the worldwide web and various applications means that the monopoly over publishing and disseminating content is gone. Gatekeepers no longer control the majority of content creation and dissemination. Anyone can create, publish and disseminate content with very little effort or investment, see this earlier post for a discussion.
Moreover, it is not just a matter of standards and quality, now given the:
- sheer number of online sources and amount of content
- ever growing group of nations, entities and individuals trying to deceive and defraud
- sophisticated and inexpensive tools that allow for the easy creation of sources and content
All content users must recognize that the online environment is flooded with substandard work and work that is either fraudulent or bordering on fraudulent and it is the user’s job to understand the quality and accuracy of the content.
How does a user go about doing this? By learning to spot red flags based on source types. Today’s post focuses on one type of issue, how to recognize legitimate journals from predatory journals.
For our purposes, the source type – journal – means a publication that present scholarly research, reviews of materials, original insights and editorial or opinion based content. Journals of this type are generally professional journals in areas such as law, medicine or engineering, academic publications that are affiliated with major universities or publications that are affiliated with a specialized industry, for example mining or oil and gas.
In contrast, a predatory journal is a journal that looks like a traditionally legitimate journal, but it is all looks. It does not adhere to established standards that further the creation and publication of quality research and materials. This is not an accident. The predatory journal is aware that it is not following established standards and it intends to mislead. These journals are mimics and in some cases complete frauds trying to mislead authors to submit their work and readers to consume and use the content as if it were quality content.
The journals are called predatory because they prey on the naiveté of the reader and in some cases the desperation of the authors that are published in these journals.
The following is a side by side comparison of some of the differences.
Contrast Between Traditional Journals and Predatory Journals

Traditional
Traditional journals are publications that present scholarly research, reviews of materials, original insights and editorial or opinion based content.
These journals are issued by publishers that are known in their fields and have a reputation and specialization in a subject matter, industry or discipline. Examples of these publishers include academic universities and industry.
The publishers of these journals:
– have strict requirements relating to the credentials and background of authors/creators/researchers.
– require a rigorousness of process for the research, creation and analysis of data and other information presented by an author.
– require that materials and sources be properly acknowledged and citations and references provided.
– often include peer reviewed articles, which means that before articles are accepted for publication the content must be vetted by a panel of experts in the same field as the author, this is a specialized type of quality control.
– do not charge authors for publication (there may be a nominal administrative fee) and do not pay for submissions.
– have processes to address issue post publication issues, including corrections and retractions.
VS

Predatory
A predatory journal is a publication, usually online, that deceptively presents itself, or disguises itself, as a traditional scientific or academic publication.
These journals falsely claim or imply that they follow standard, accepted publication standards, including peer and editorial reviews.
They may also claim or imply affiliations with legitimate journals and institutions and claim to be in scholarly indexes.
These journals are operating in a way to deceive readers.
The journals are also “preying” on the need for authors to publish as part of their professional credentials and reputation.
The issuers of these journals may:
– aggressively spam and contact authors to solicit submissions.
– lack quality control and not apply standards and guidelines for publication that match traditional journals.
– accept materials without rigorous reviews such as peer review process or editorial board process
– publish content or data that is falsified, plagiarized or lacking scholarly content.
– charge authors large fees to be included in the publication.
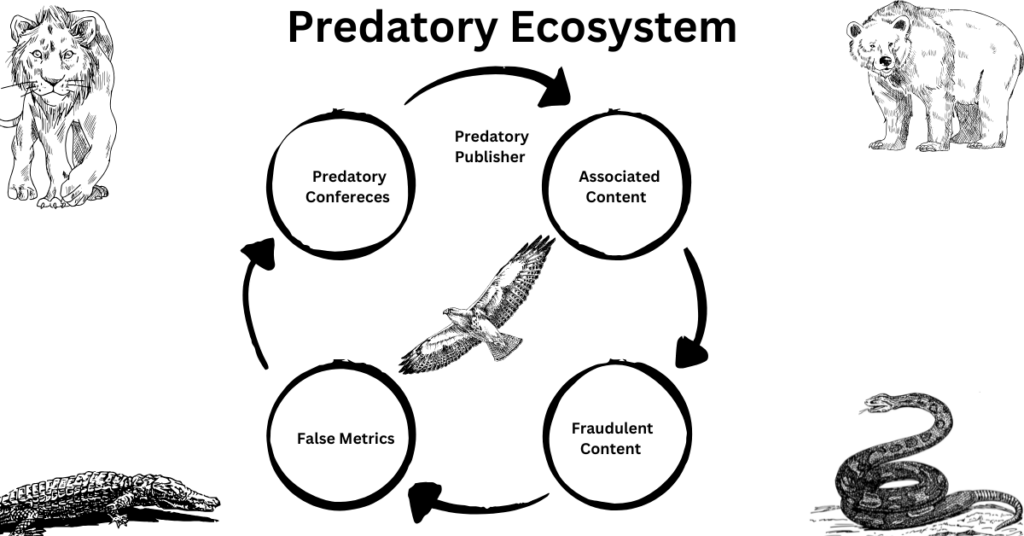
The Ecosystem of Predatory Journals
Predatory journals exist to make money. They make money by charging authors and by charging readers.
It is also vital to recognize that these journals often exist within an ecosystem. The journal is just one component. Additional components, which produce income and be used to create a false reputation, include:
- Associated Content – there may be thousands of articles and hundreds of journals associated with a single publisher.
- Fraudulent Indexes – within different fields there are legitimate indexes which list journals and articles that meet the standards associated with traditional journals. These indexes are used by researchers to find relevant content. A journal’s inclusion in a recognized scholarly index indicates quality and it enhances the journal’s reputation and academic influence. Creators of predatory journals may create fictional indexes that mimic legitimate indexes. The goal is to lure researchers and readers into believing that the journals are reputable because they are listed on an index and to enhance the standing of the journal.
- False Metrics – Again, within different specialized fields, there are metrics that are used to judge the impact and credibility of the content of a particular journal. Creators of predatory journals may also create false metrics to inflate or fabricate the standing of their articles and journals. For example, there are metrics that measure the number of citations made to a particular article. The idea being that the more citations in the field the more credibility has given to the material. False metrics may be created to fabricate or exaggerate citations to an article in a predatory journal.
- Predatory Conferences – These are events that are organized to extract registration fees from presenters and attendees. The quality of the speakers and the materials presented do not meet the traditional academic or research criteria for these types of events
These journals and their ecosystems do not exist to advance knowledge, disseminate useful information or advance the understanding of a field of study and they are not benign. The content contained in these journals is at best unvetted and at worse fraudulent.

Spotting The Predators
Once you understand that these journals exist, spotting the journals requires the same skills and diligence that you apply to any new source.
This includes:
1. Looking for obvious red flags, here are some:
- Is the publisher publishing hundreds of journals on multiple unrelated topics?
- Is the name of the journal an obvious dupe or copy of another journal?
- Are there typos or misspellings and other evidence that the work has not been copyedited?
- Does the work properly cite materials?
- Is the quality of the writing as expected for the level of expertise in the specialty?
- Does the article title make sense both for the article but also for inclusion in the specific journal?
- What does the associated website look like? Is it professional, does it contain all the information that is expected, including names of editorial staff and board, publication and review standards, contact information and is this information consistent with stated locations and venues.
2. Performing diligence on the:
- publisher of the journal
- editorial staff (be aware that names may have been used without permission or even fabricated)
- journal
- creator/author of the content
- the content
2. Consulting online lists
- There are online databases of recognized scholarly journals that you can consult when you have the name of a journal. However,
- you need to identify that the database you use is considered authoritative
- there may be a charge to use the database
- predatory journals have found their way on to some of these databases even though they attempt to keep them off the database and do purge. There is a summary of these issues in the American Journal of Medicine.
- Google Scholar does not exclude predatory material. Therefore it is not a database that can be used to exclude a journal or article from the journal as predatory. Google Scholar indexes content that appears to meet its subject matter and source criteria. It does not exclude or even identify as being predatory.
- There are online databases of identified predatory journals.
- The most well known list was started by Jeffrey Beall a librarian at the University of Colorado. Beall’s List is no longer affiliated with him and it does not grow, but it is maintained by an anonymous source.
- There are commercial databases such as Cabells that require a subscription by an organization. This page from Old Dominion University is directed toward authors but contains useful information for readers as well.
3. Consulting experts
You may not be able to spot a predatory source if you don’t have the specialized knowledge relating to the topic of the journal. In these circumstances you need to consider consulting an expert. Some things to consider include:
- Importance – how central or important is the specialized knowledge to your diligence, obviously if it is important or key, you need to make sure that subject matter expertise is part of the diligence team.
- Your knowledge – if you are not in a position to identify a predatory source, are you sufficiently knowledgeable to identify, understand and analyze non-predatory material?
- Organization requirements – your organization may have internal requirements that specialized knowledge or assistance be involved with certain types of diligence. For example, if you are performing enhanced due diligence relating to economic sanction laws, the legal or compliance departments may need to provide guidance or feedback.
4. Online Resources
There are a number of online resources that provide lists of ideas of how to determine if a journal is predatory. Universities have an interest in making sure that their population are aware of the issues relating to use of sources published in predatory journals as well as the submission of their research to predatory journals. Here are some examples:
University of Texas – MD Anderson Cancer Center – Q. How can I determine if a journal is predatory?
The University of Arizona – Identifying Predatory Publishers
Old Dominion University – Library Guides – Where (and Where Not) to Publish Your Work
SUNY Oneonta – Milne Library – Predatory vs. Legitimate Journals
Some Additional Thoughts
Change – it is possible and has been reported that there are journals that began as legitimate journals and slid into becoming predatory journals. You need to be alert to this possibility each time you use a journal don’t just rely on past diligence, it is not once and done.
Fake/Hijacked/Cloned Journals – Predatory Journals are not the only types of journals that are misleading. There are online publications that counterfeit existing traditional journals. The goal is to fool readers into thinking they are reading the journal that is being faked, and to induce authors to pay to submit their work to the fake journal. The ways in which the scammers accomplish impersonation are growing in sophistication and can include fake domain names, redirected links from academic database listings and indiscriminate search results.
Evaluate – This is a post about how sources that appear reputable may not be reputable. The way to prevent being taken in by a source is always the same, you need to conduct an evaluation of the source. That includes the publisher, the author and the content so that you are comfortable that the source quality is acceptable for your diligence project. This concepts is discussed in this post – It’s Content Judgement Time – Are you up to the task?
Verify – If you have any doubts, verify the source and the content provided by the source. For example you would want to verify if:
- you cannot recognize or validate the reputation of the source, in this case a journal
- you have questions about the knowledge level or expertise being presented
- the quality of content appears questionable
- the content does not seem complete
- you remain unsure, skeptical or uneasy about the reputation of the source or the quality of the content, advice or other information provided.
Verifying means you look for other sources to confirm what you have already found. Never hesitate to verify, if needed verify with multiple other sources. And if still in doubt understand the doubt as a point of clarity – you have a found a source that does not meet your standards.
Sign Up to Receive the Diligence File Emails – More Ideas & Resources to Advance Your Diligence
Thank you


Subscribe for Diligence Updates
Get the latest updates, resources, offers, and more.
"*" indicates required fields
The Diligence File respects your privacy. Privacy Policy